This information is intended for all Duke Community members and is a continuation of the initial alert.
Summary
Threat actors are distributing malware through a technique known as ClickFix by tricking users into copying and executing malicious code in a terminal or command prompt. These attackers have been seen using fake CAPTCHAs, misleading error messages, or other fraudulent pop-ups. Once executed, the code downloads malware from a malicious site, stealing passwords, cookies, cryptocurrency wallet details, and other personal and financial info. In addition, attackers are also leveraging social media to trick users.
Problem
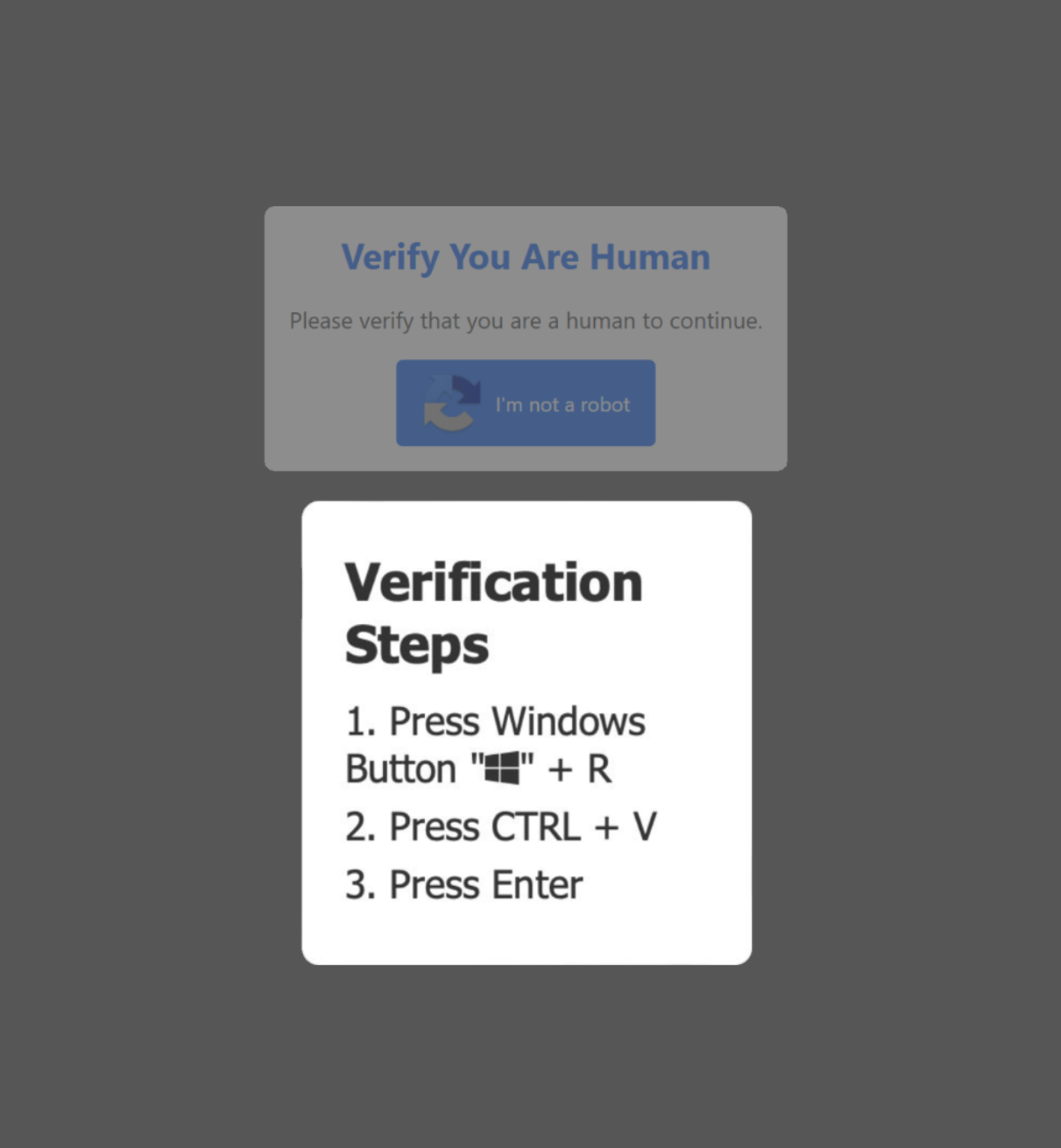
A fake CAPTCHA is a security challenge designed to look like a legitimate CAPTCHA but is a scam. Its purpose is to trick users into executing malicious code on their device, which can lead to malware infections and data theft.
A fake error message or pop-up is a dialogue box that is designed to look like a legitimate error or warning but is fraudulent. Its purpose is to trick users into executing malicious code, downloading malicious software, or visiting a malicious site.
Threats
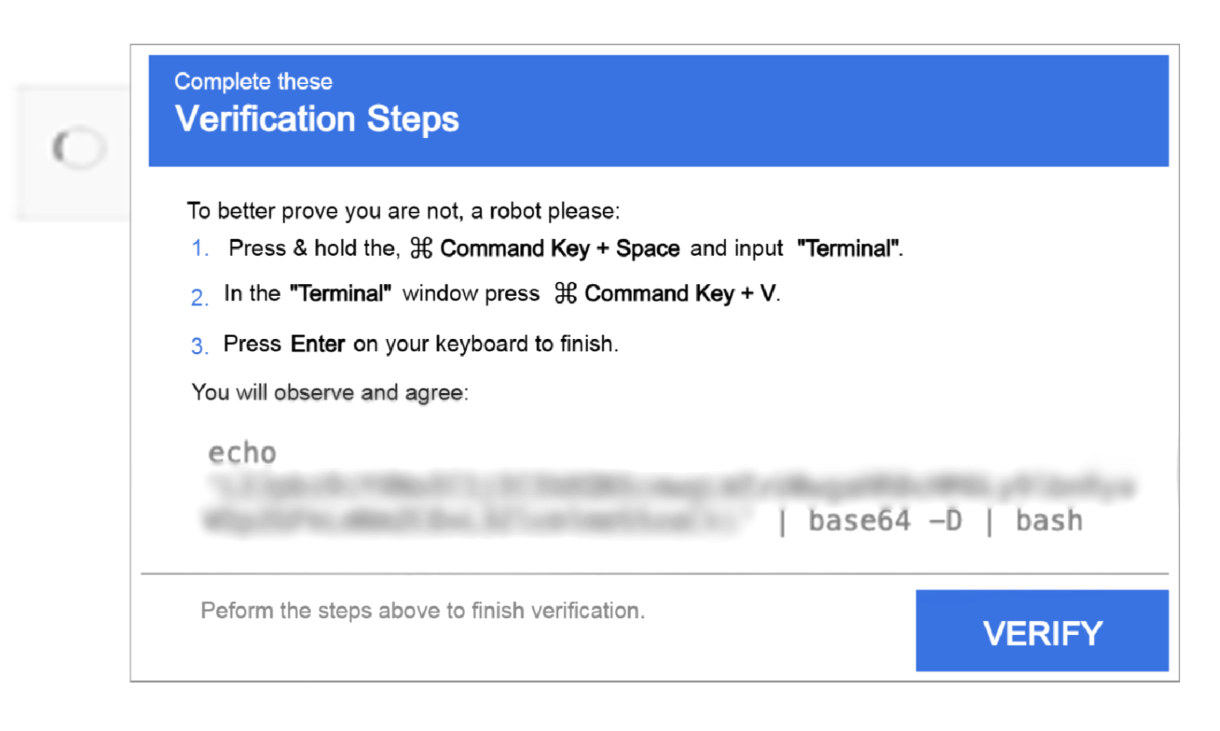
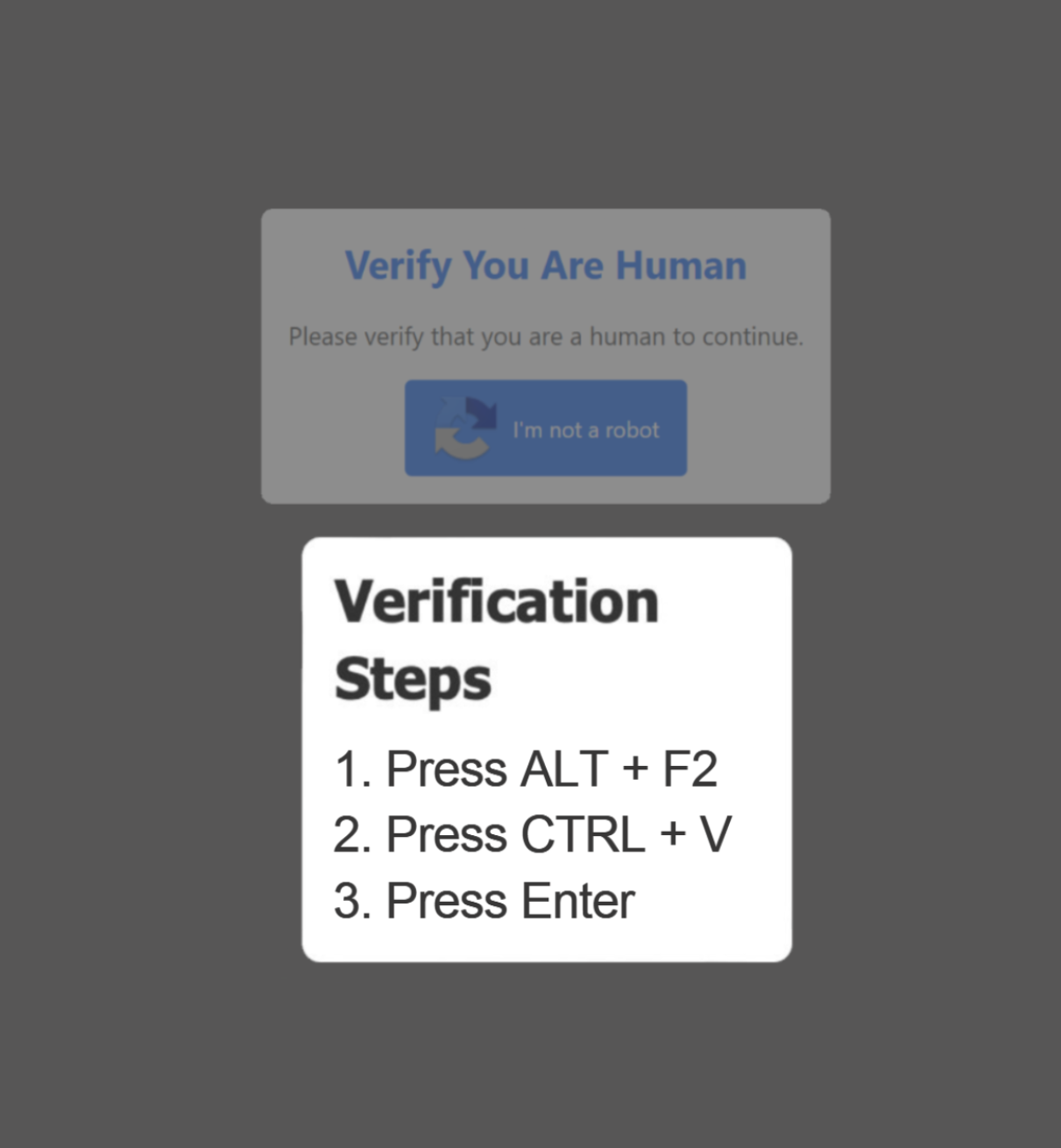
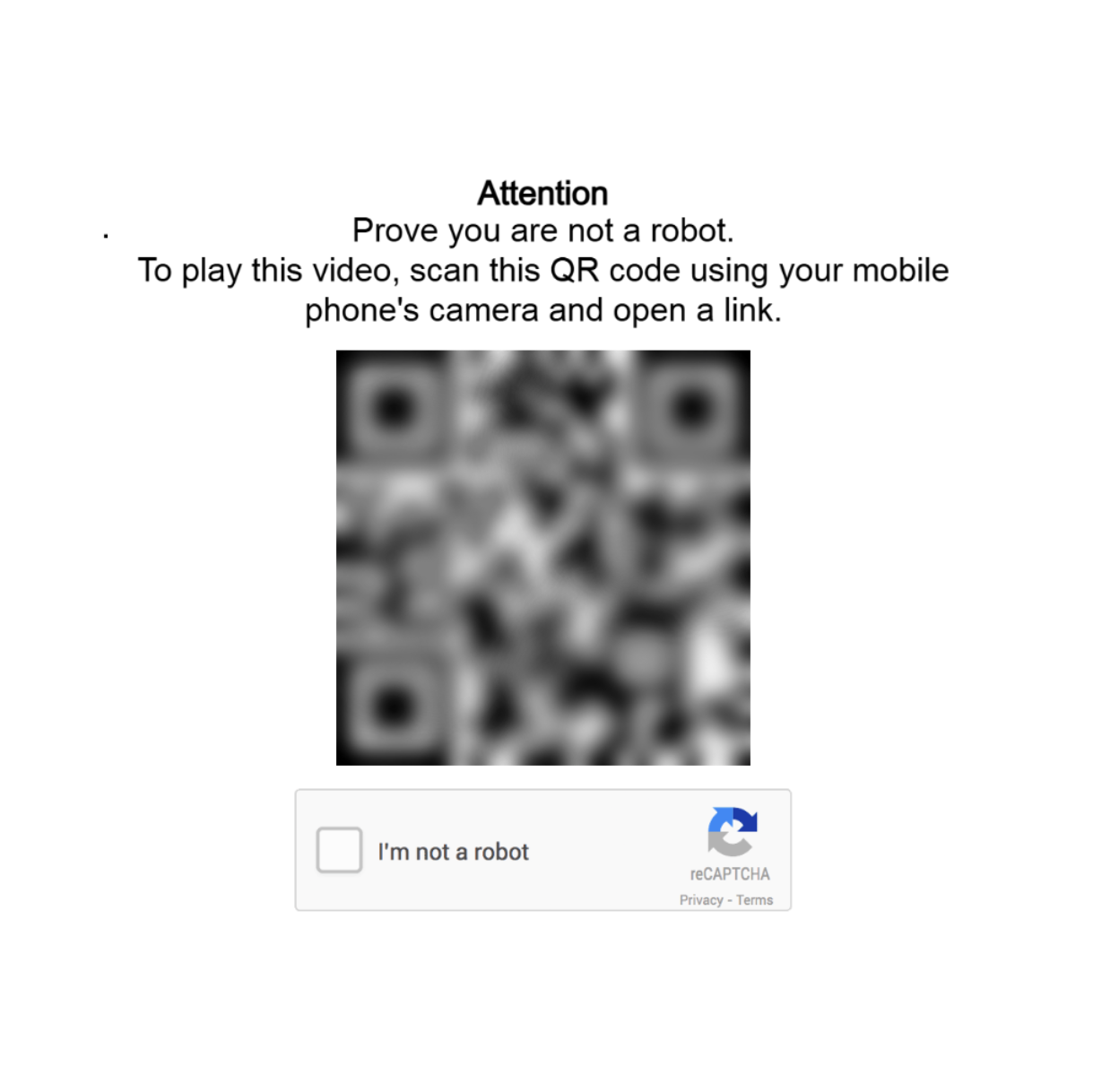
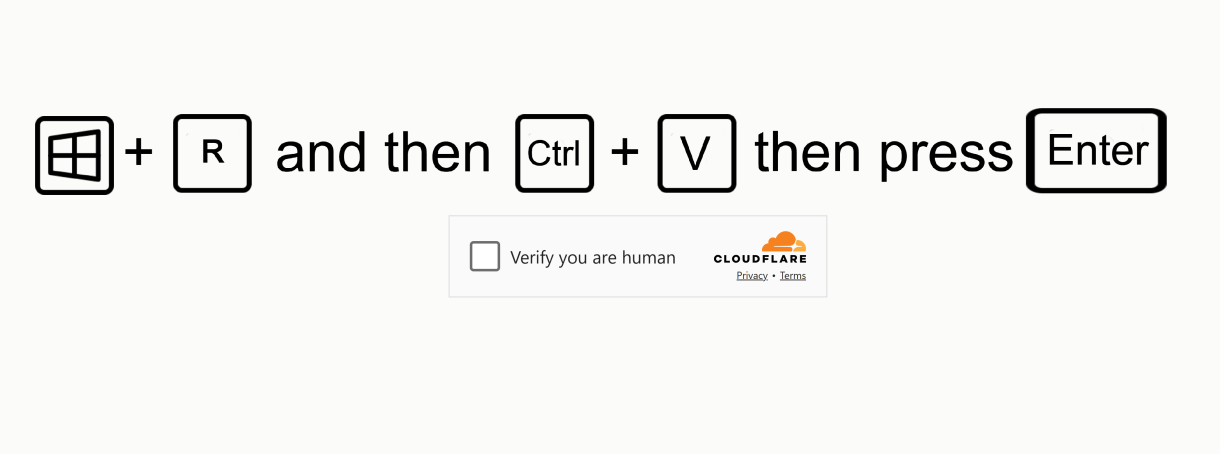
Fake CAPTCHAs prompt users to “verify they are human” by copying and pasting code or scanning QR codes that link to malicious scripts.
|
Image
 |
Image
 |
Image
 |
Image
 |
Image
 |
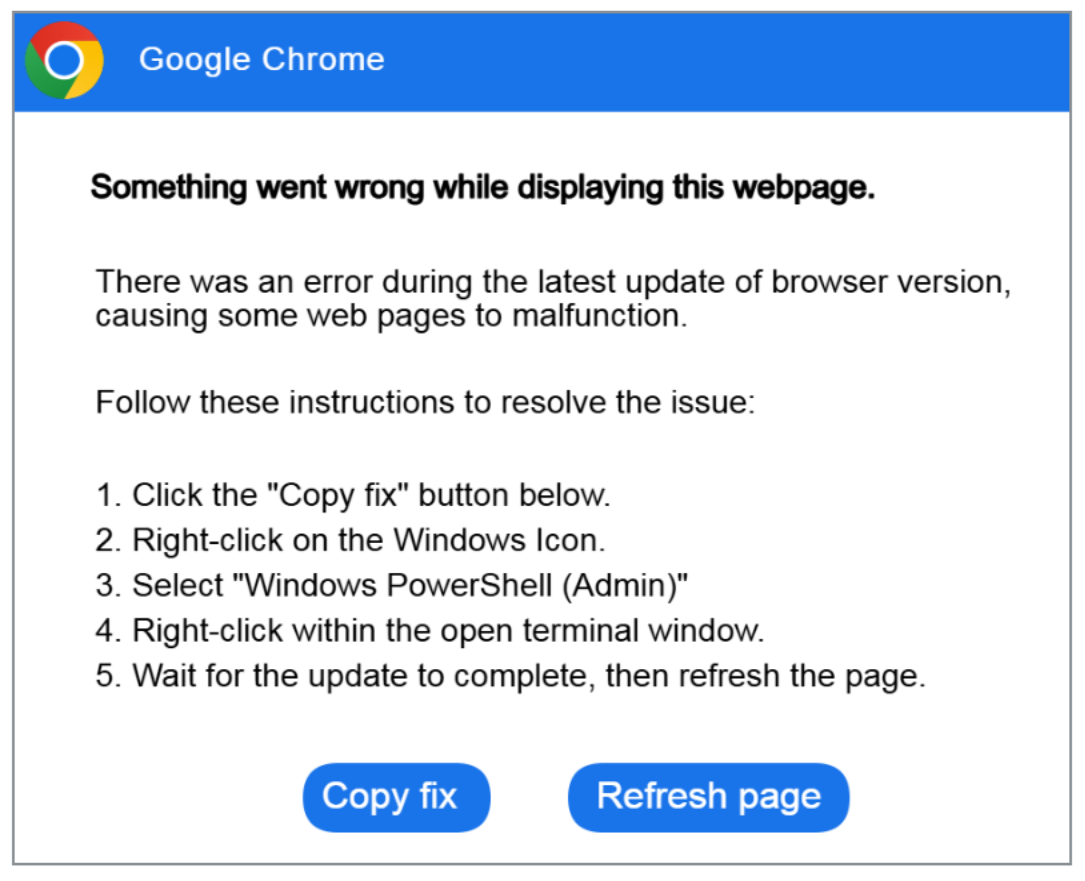
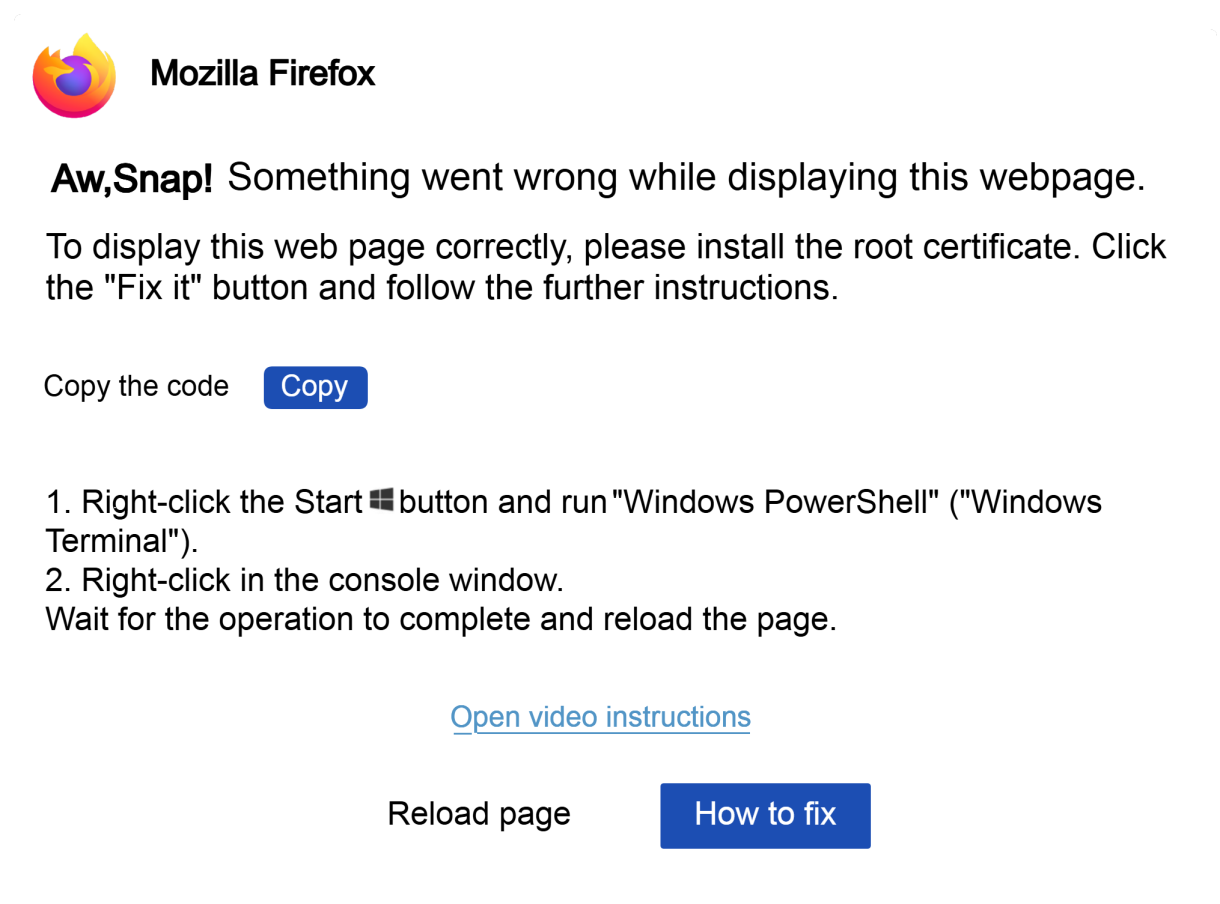
Fake Error Messages and Pop-ups claim a problem or issue can be fixed by running a command.
|
Image
 |
Image
 |
Image
 |
Image
 |
Image
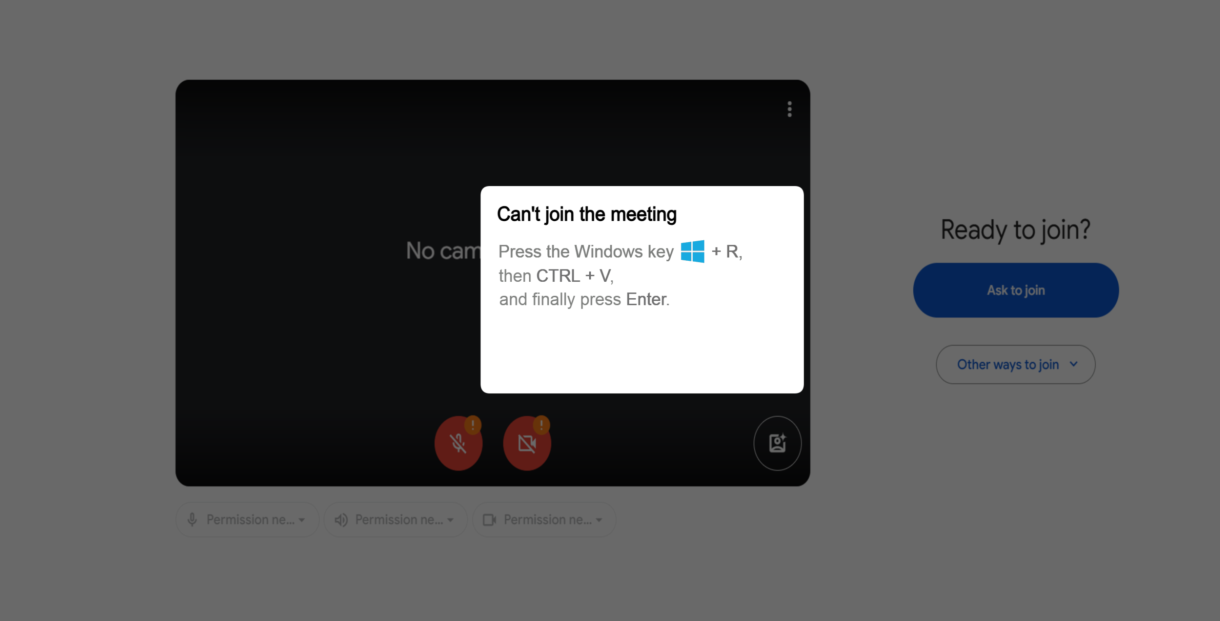 |
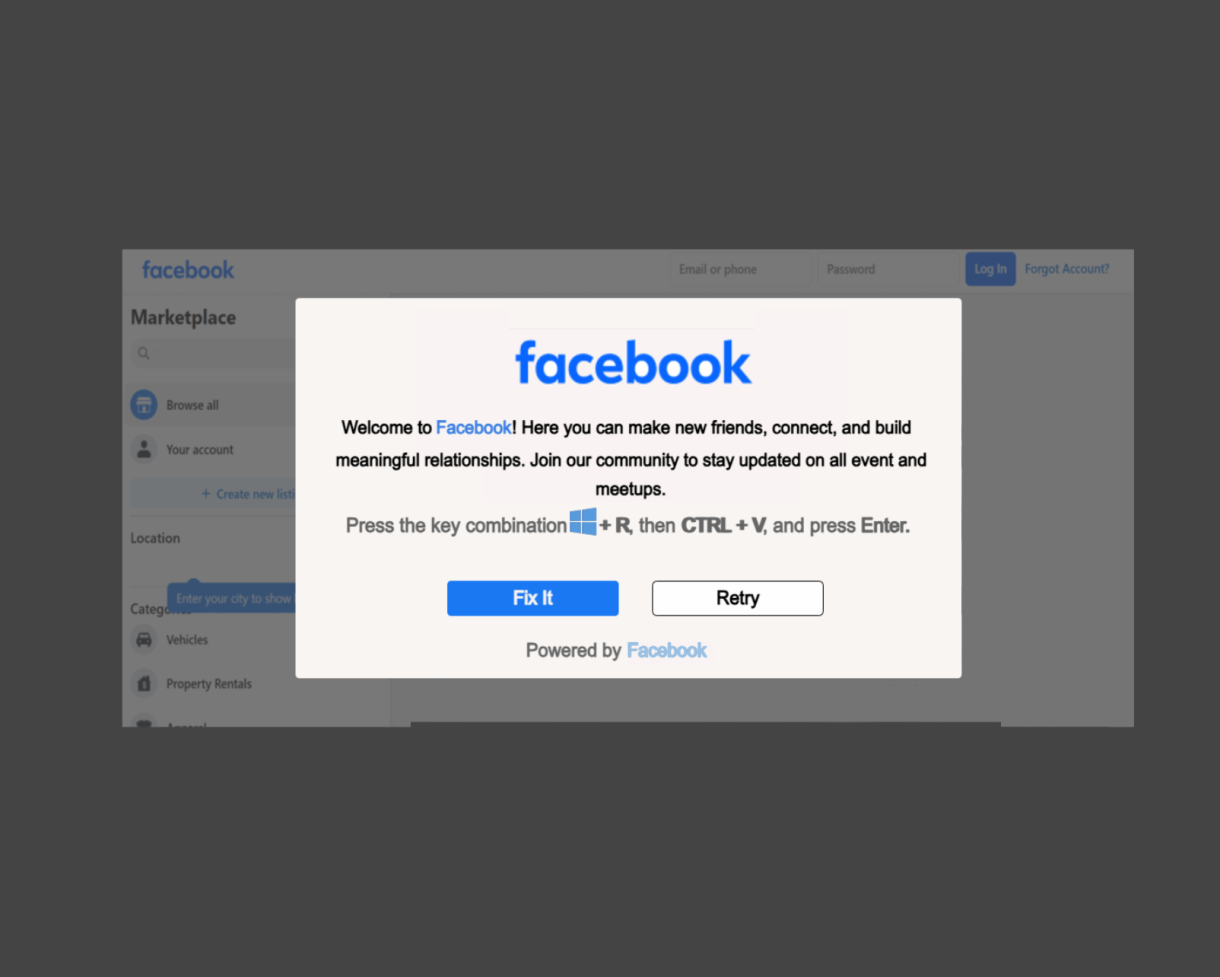
Malicious social media posts are used to encourage users to run suspicious code under false pretenses such as obtaining free software or fake job postings.
|
Image
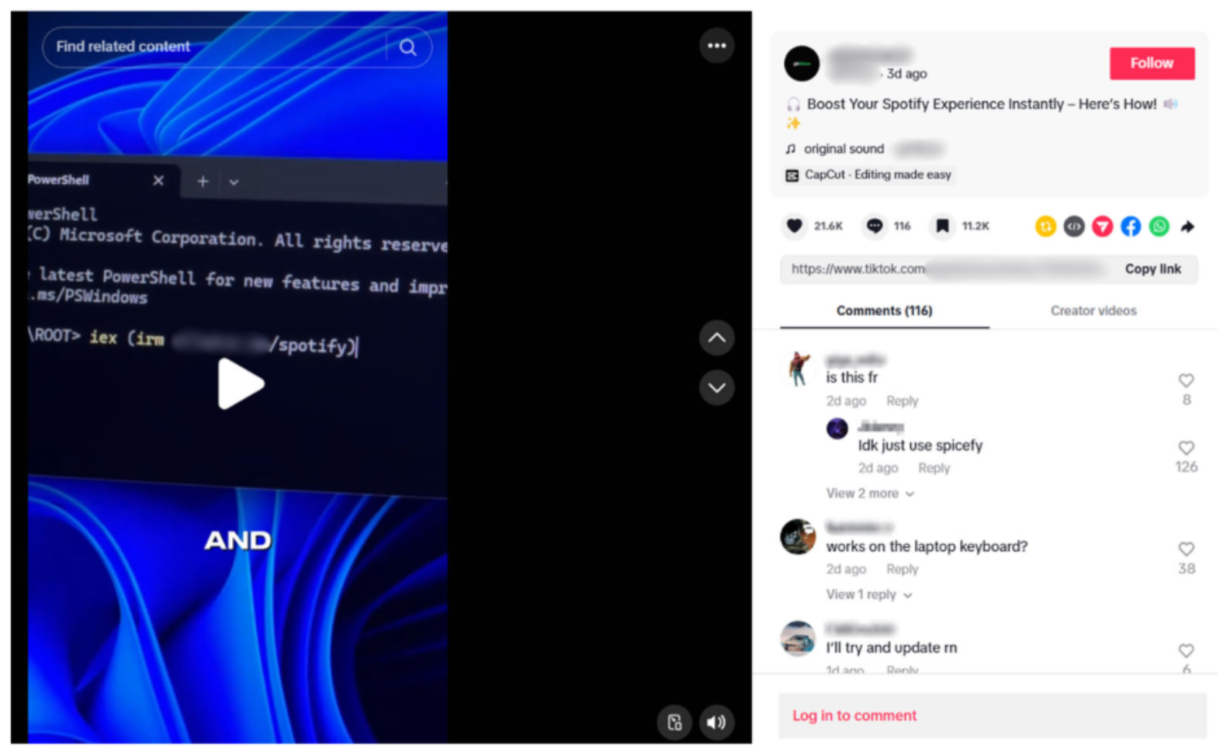 |
HOW WE PROTECT DUKE
- Avoid interacting with CAPTCHA pages or error messages that seem out of place or unusual.
- Be cautious of suspicious CAPTCHA pages or error messages.
- Block Pop-Ups using your browser settings.
- Clear the clipboard because it likely contains an executable command.
- Duke will never ask you to perform commands in an email or on a website.
- Never execute Terminal commands prompted by websites through CAPTCHAs, error messages, or other verification interfaces.
- Update your software and applications.
if you spot one
- Take a screenshot of the CAPTCHA or error message and report the page you were visiting to security@duke.edu and any additional steps you may have taken.
- If you got to the site by clicking a link in an email, use the “report message” button.
ReferenceS
- 1Password: DOM-based extension clickjacking
- Behind the CAPTCHA: A Clever Gateway of Malware
- ClickFix Social Engineering Technique Floods Threat Landscape
- Fake CAPTCHA websites hijack your clipboard to install information stealers
- Hackers now testing ClickFix attacks against Linux targets
- HC3: Sector Alert October 29, 2024 TLP:CLEAR Report: 20241029150
- Lumma/Amadey: fake CAPTCHAs want to know if you’re human
- Over 2,800 Hacked Websites Targeting MacOS users with AMOS Stealer Malware
- TikTok Videos Promise Pirated Apps, Deliver Vidar and StealC Infostealers Instead
- This CAPTCHA Test Can Trick Windows Users Into Installing Malware