What is a Data Breach?
A data breach is when a threat actor has gained access to sensitive information such as your passwords, usernames, SSN, IP/geolocation, phone number(s), credit card information, or other data.
Numerous high-profile data breaches have occurred at external organizations such as: Chegg, Equifax, Facebook, LinkedIn, National Public Data, and Yahoo.
What is Password Reuse?
Password reuse is when the same password is used for more than one account. For example, when the same password is used for both Facebook and Gmail. It is advised to avoid using the same password on multiple accounts. Your Duke password should be unique and a password from an external site should not be reused here at Duke.
Why does this matter?
Hackers can use a password that they obtained from an external data breach pertaining to one account and attempt to access other accounts with the same password leading to further account compromise. The more often a password is reused, the more opportunities there are for attackers to gain unauthorized access to systems and steal data and perform other malicious activities.
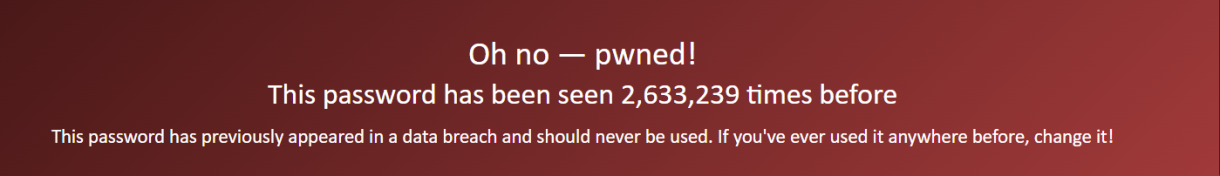
For example, the password 1234 has been seen 2,633,239 and is categorized as a weak password.

What does it mean if your password was found in a breach?
This means that the password has been identified and published in online databases as being compromised through a data breach that occurred outside of Duke. In other words, the password should not be used for any account, as it is a known password and therefore likely to be used by attackers to help gain unauthorized access in the future.
What should you do?
If your password was found in a breach, check all your accounts that use that password and change it. Hackers sell stolen data, including passwords, to other hackers. So, once a password is exposed, don't use it or any variation of it again.
What are some best practices?
Best practices to protect against potential account compromise include: ·
- Set up Multi-Factor Authentication (MFA) for all accounts. Having an extra step in verification can prevent unauthorized account access.
- Use a password manager tool (1Password) to help manage, store, and create unique passwords.
- Check if your accounts have been compromised using haveibeenpwned (a free data breach search service), and the Watchtower tool within 1Password.
- Reset your passwords and do not use a variation of your old password.
- Duke provides the account self-service tool, which checks against known compromised passwords, if you believe your Duke account(s) have been compromised.
Questions?
The security office is here to help and can be contacted by emailing security@duke.edu